
Audit Consulting & Advisory Services
ISO 27001 certification helps organizations to setup a security framework and implement...

We conduct Vulnerability Assessments to identify, quantify, and classify the security vulnerabilities of your computer...

Penetration testing (ethical hacking ) attempts to exploit critical systems and gain access to sensitive data...

Public-facing web applications are still by far the top concern for developers and managers of applications...
Audit Consulting & Advisory Services
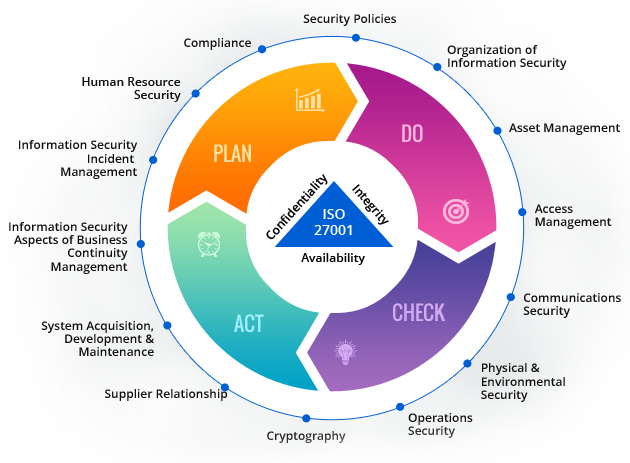
ISO 27001 certification helps organizations to setup a security framework and implement all the controls to mitigate, control, and eliminate vulnerabilities. Our methodology and proprietary product will help customers to track, report and remediate compliance against security controls with minimal efforts. We also provide Integrated Standards Management System incase you have multiple standards in place in your organization and need an integrated approach to the ISMS.
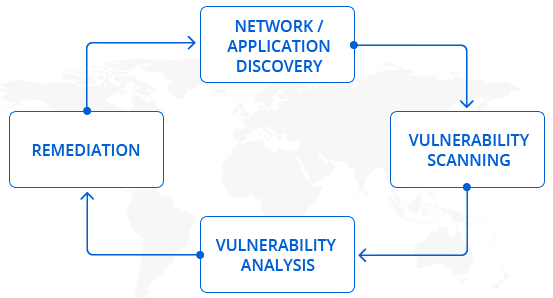
We conduct Vulnerability Assessments to identify, quantify, and classify the security vulnerabilities of your computer, network, or communications infrastructure. Exploitation of these vulnerabilities will result in unauthorized access to confidential data and information and pose a threat to your organization.
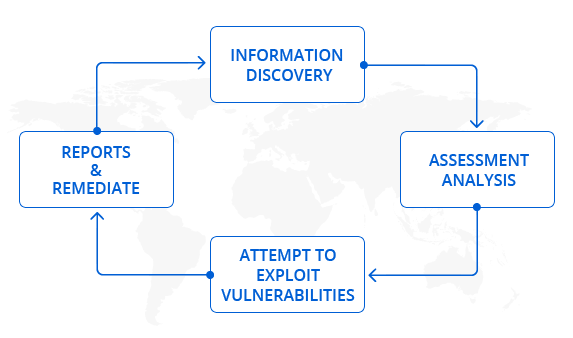
Penetration testing (ethical hacking ) attempts to exploit critical systems and gain access to sensitive data using many tools and techniques. If a system is not secured, then any attacker can disrupt or take authorized access to that system.Our Methodology of Network Penetration Testing Includes two possible scenarios: Externally from the Internet facing the customer network and Internally in the customer network.
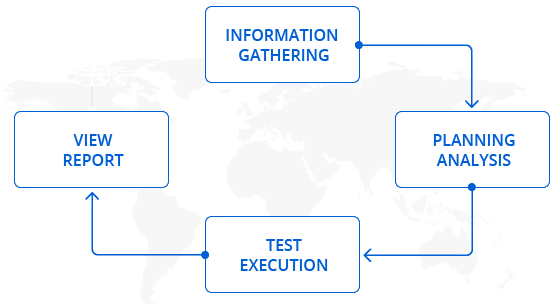
Public-facing web applications are still by far the top concern for developers and managers of applications, we identify potential or realized weaknesses as a result of inadvertent mis-configuration, weak authentication, insufficient error handling, sensitive information leakage, etc in your websites, web applications and web services through web application security testing.
Certified ISO 9001:2015 Company

